by Jamie O’Mahony
KX has a broad list of products and solutions built on the time-series database platform kdb+ that capitalize on its high-performance capabilities when analyzing very large datasets.
KX for Surveillance is a robust platform widely used by financial institutions for monitoring trades for regulatory compliance. The Surveillance platform instantly detects known trading violations like layering, spoofing or marking the close. Customers can calibrate their parameters in real time to improve their detection quality and accuracy. The flexibility of the historical database and replay engine eases retrospective investigation for new types of fraudulent behavior and suspicious activity.
In this series, we take a look at what makes KX for Surveillance such a powerful tool for detecting market manipulation. The first article in the series takes a close look at spoofing and layering alerts and describes how time-series analytics and parallelization are powerful features for detecting fraudulent behavior.
Spoofing and layering, like many other forms of market manipulation, can have slightly different interpretations depending on who you talk to. While some use the terms interchangeably, others distinguish between them by defining spoofing as manipulation occurring at top of the book only, whereas layering occurs at multiple price levels. There is consensus, however, on what they both entail – the deliberate distortion of market prices by placing deceptive orders that do not reflect true trading intent. Their purpose, instead, is to inflate (or deflate) prices by creating an illusion of extra demand (or supply) in the marketplace that induces or tricks other market participants to make similar trades. Such trades then further distort the price and enable the manipulator to create an illicit profit by opportunistically trading in the opposite direction at more favorable prices than would otherwise have prevailed without the deceptive behavior.
The rise of high frequency trading (HFT) gave firms the opportunity to engage in spoofing and layering across many markets, and while the practice had been particularly prevalent in the US equity markets, it is now on regulators’ radars across all sectors.
“Layering is a deceptive practice to trick others into buying or selling a stock at artificially inflated or depressed prices,” said Daniel M. Hawke, Chief of the SEC Enforcement Division’s Market Abuse Unit. “No matter where they are located, we continue to identify and investigate those whose trading practices threaten to undermine the fair operation of the U.S. securities markets.”
So what exactly is needed to detect activities such as spoofing or layering and what attributes does a supporting solution architecture require? Below are some examples from the KX for Surveillance solution used by regulators and bank compliance departments worldwide to ensure trading and market integrity.
Processing large data volumes
As with many forms of market manipulation, detection of spoofing and layering involves looking for patterns in data – lots of data. A typical approach involves analyzing all internal order/quote actions and trades along with market quotes (not just top of book but also the depth) and consolidated trades in order to determine whether the deceptive orders and cancellations that form part of the strategy were actually marketable (i.e. likely to execute) at the time of transaction. This can consist of hundreds of millions of records when focused on equities or forex, and moving to options market analysis can increase the volume ten-fold.
Many products and technologies struggle in processing even a subset of the data at these volumes. In contrast kdb+, on which the KX for Surveillance solution is based, has been used for the past 20 years in processing huge financial datasets that can typically exceed petabytes (1015 bytes) and can process the required volumes with ease.
Time series capabilities
Pattern identification often needs supporting metrics to further investigate and qualify the underlying activity. With spoofing and layering, for example, the concept of a marketable quote is important as an order placed too far from the top of book would have little likelihood of being executed, and therefore would not potentially induce interest from other market participants. However, the marketability of a non-bona fide quote is not a static calculation as it varies from stock to stock and over time. Therefore the time series nature of kdb+, and its programming language q, is ideal for its computation by facilitating swift calculation of exponential moving averages and other time-based statistical benchmarks.
Temporal joins are another time series feature of kdb+ that are particularly powerful in identifying various forms of manipulation. The first in-built temporal join, aj (asof), can be used to quickly identify the prevailing best bid/offer at the time of any internal order action. The second in-built temporal join, called the window join, is similarly invaluable in recreating a view of the market around the time of cancellations.
The window join is a generalization of the asof join and grants the ability to calculate market metrics within the defined intervals. The window join is capable of computing the required metrics over very granular time intervals (for example one second windows over the six and a half hours of the open market) at extremely efficient levels and within timeframes of a few seconds. The flexibility to define and reconfigure such intervals in real time gives further power to the solution in being able to react swiftly to changing market conditions
Exception monitoring and alerts management
Based on SEC or CFTC findings, it is apparent that firms typically execute their spoofing and layering practices over periods of days, weeks and months. Therefore the person of interest has to be seen implementing this behavior of cancellations and contra side executions a number of times in order to be confirmed and promoted to the status of an alert. Surveillance systems must therefore monitor the trend of such apparent violations and flag concern only where a pattern is discernible.
Excellence in exception monitoring and alert generation control in this manner is crucial for many other market manipulation investigative cases too. In its absence investigators would either be left unaware of insidious intent underlying apparently normal trading activity or overwhelmed by false positives that were in fact simple market aberrations and not indicative of any malpractice.
Parallelization
Because spoofing, layering and many other forms of market manipulation do not contain interdependencies between stock ticker symbols it is possible to distribute the processing of data across multiple server cores. Within KX for Surveillance dedicated subscriber engines along with parallelization of slave threads enable independent simultaneous processing of analytics to monitor, identify and alert users to suspicious and proscribed market trading activity. In a market where speed of execution provides the competitive edge, speed of detection helps brokers and regulators ensure it remains legitimate.
Conclusion
Investigation of alerts can be difficult and time-consuming and often requires detailed analysis of circumstances surrounding their trigger events – what market events had occurred, what communications were made, what behavioral changes were seen. In addition to the above mentioned processing capabilities, the ability to replay events and recreate market conditions using powerful, yet flexible, and easy-to-use dashboards, like the KX for Surveillance example shown below, significantly enhances investigators insights, accuracy and efficiency.
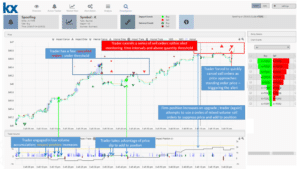
For more information on KX for Surveillance and its functionality please click on the links below.





