by Brighde Mulholland
All good developers involved with production systems know the criticality of building secure and fit-for-purpose releases. Security configuration isn’t always the most exciting or glamourous aspect of a developer’s workload, but as recent high-profile data breaches show, it may even be the most important part of the jobT.[1]
In this blog I will detail five easy, out-of-the-box configurations that will ensure the security of your application specific instance of the KX platform. They will address the following security configuration options, which should be set to the OWASP (Open Web Application Security Project) recommendations:
- Configurable UI Session Timeouts
- Preventing Malicious File Uploads
- IP Access Restrictions
- URL Access Restrictions
- Configurable Password Policies
The majority of these changes require ‘DELTADASHBOARD_PASSWORD_POLICY=yes’ in the delta.profile, so it would be best to confirm this before you begin.
- Configurable UI Session Timeouts
The first configuration is restricting the session timeout of the KX Platform. OWASP recommends an idle timeout range of 2-5 minutes for high-value applications and 15-30 minutes for low risk applications.[2]
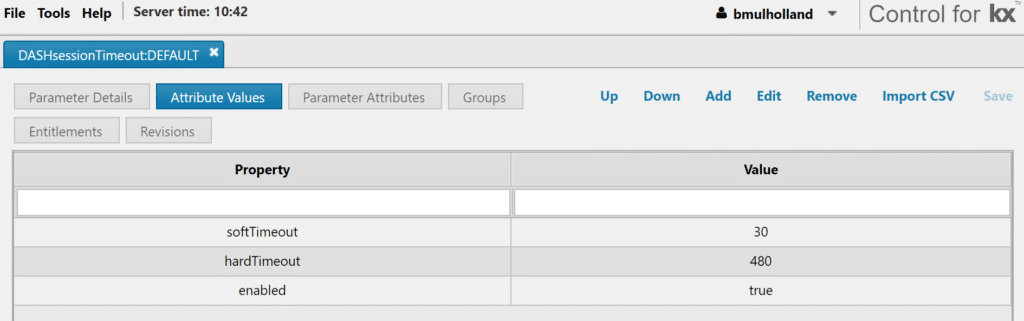
- Open the DASHsessionTimeout:<DEFAULT> configuration parameter in Control for KX. After restarting the platform, the enabled property should be set to “true”. The “softTimeout” property, will disconnect a user if they do not query the database within the value period (in this case 30 minutes). This will be affected by polling dashboard queries, so managed queries should be used instead when implementing this functionality.A “hardTimeout” occurs regardless of user activity on the dashboard, so it is not affected by polling queries. The hardTimeout set below is for 8 hours. Both properties can be configured on a user basis, allowing administrators to potentially have a longer period before the session disconnects due to inactivity (softTimeout) or elapsed time (hardTimeout).
- Preventing Malicious File Uploads
The file upload functionality available via Dashboards for KX can be integrated with clamAV to allow configurable support for virus scanning all files uploaded to the platform environment.
- Install ClamAV on the server where the dashboard and tomcat packages are installed. This can be pointed at /delta-data/fileStore/tmp directory.
- Update the DELTAAPPSERVER_VIRUS_SCAN_ENABLED to “true” in the delta.profile and restart Control for KX.
- This can be tested by attempting to upload a benign malware/virus such as the test file from European Institute for Computer Anti-Virus Research (EICAR)[3].
- If you require large files to be uploaded, you can increase the file size by changing the MaxFileSize and StreamMaxLength parameters in clamAV.
- IP Access Restrictions
IP restrictions can be added on a user group basis in Control. This will prevent users in this group from accessing the Platform UI’s unless they are connecting from a whitelisted IP. This is useful if you have a requirement to prevent certain user’s access if they aren’t on the network.
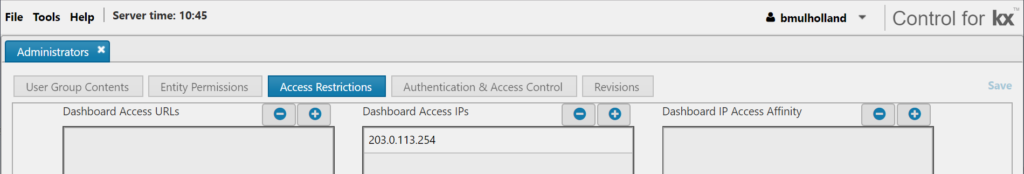
- Open the relevant User Group in Control and under Access Restrictions select the Dashboard Access IPs tab. Edit the IP range you wish to whitelist using the plus and minus row options. When editing is finished save the user group to implement the changes.
- This can be implemented for access to Control for KX using the IP Access Affinity tab instead of Dashboard Access IPs.
Following these changes users attempting access from an unapproved IP will get an “Invalid IP” error on attempted login.
Environments that use netscalers, may need to enable passthrough mode (on the netscaler) to allow the end users IP through to the platform for authentication.
- URL Access Restrictions
Another form of access restriction can be implemented by allowing a user group access to specified urls only. This is extremely useful for allowing a certain user group access to Dashboards in viewer rather than edit mode (where queries and dashboards could be modified).
This quick implementation is even faster if you’ve already added IP restrictions and is recommended in the OWASP Top Ten.[4]
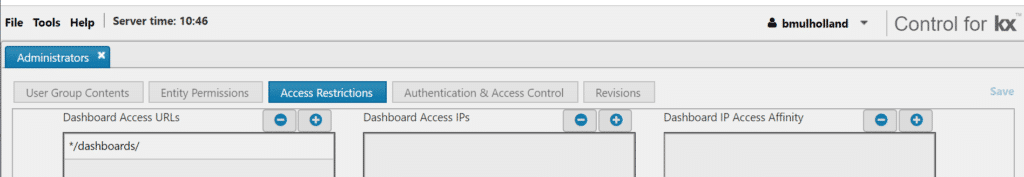
- Open the relevant User Group in Control and under Access Restrictions select the Dashboard Access URLs tab. Here, you can add any url you would like the user group to have access to. For example, if you would like a certain user group to only have access to Dashboards Viewer, add */dashboards/. If you would like access granted to edit mode, then whitelist /dashboards/edit.
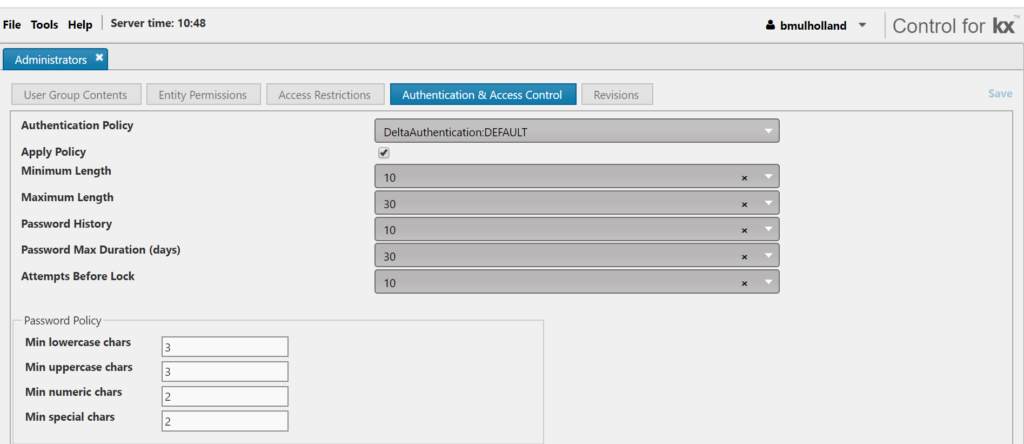
- Configurable Password Policies
The KX Platform also offers the functionality to enforce a password policy on a user group basis. This is especially useful when using the “forgot password” functionality introduced in release 4.0.0. Enforcing a strong password policy can help in blocking brute force attacks.[5]
- Open the relevant user group and go to the Authentication and Access Control Tab. Check you have selected an authentication policy from the dropdown and ticked the box to apply a security policy of your choosing. Note: you can’t leave any of the options blank or you won’t be able to save your changes.Required fields include, minimum and maximum password length, password history (how many new passwords you need to use before you can reset it to an old one), maximum password duration (forces a change of password after a certain day period) and allowed attempts before locking the user. This will lock the user out of the platform after a certain number of failed attempts. They can be unlocked by a permissioned user via Control.The security policy functionality also allows a user to specify password requirements for a user group. These include minimum lowercase, uppercase, special and numeric characters. OWASP recommends certain levels of password complexity and defines what a strong password policy should contain[6].
So, there you have it, 5 simple suggestions to enforce the security of your application specific KX platform install.
[1]https://www.businessinsider.com/data-hacks-breaches-biggest-of-2018-2018-12
[2]https://https://www.owasp.org/index.php/Session_Management_Cheat_Sheet#Session_Expiration
[3]http://2016.eicar.org/86-0-Intended-use.html
[4]https://www.owasp.org/index.php/Top_10_2010-A8-Failure_to_Restrict_URL_Access
[5] https://www.owasp.org/index.php/Blocking_Brute_Force_Attacks
To learn more about KX solution please click on the links below.